IPTables & Netfilter#
Been wanting to write this one for awhile. Let's take a look at iptables and netfilter. We will look at their relationship and how they function.
What is the relationship between IPtables & Netfiler?#
IPTables is Linux based network firewall that uses the Linux kernel packet filtering framework called Netfilter. Besides packet filtering, Netfilter also has NAT capabilities, packet logging & packet mangling features. Thus with IPtables using it as a framework it also has these same capabilities.
An IPtables firewall interacts with the netfilter framework hooks to perform packet filtering. Packets that travel through the network stack will trigger these hooks. IPTables uses these hooks to ensure traffic follows the conditions laid out within the firewall rules.
Netfilter Hooks#
Netfilter has 5 hooks that can be used to help with traffic decisions. They are registered with the Linux kernel to be called at specific points in the network stack. The hooks that are triggered are all based on the direction of traffic, destination and if the traffic was dropped or rejected.
-
NF_IP_PRE_ROUTING - Triggered by incoming traffic soon after entering the network stack. This hook is triggered before any routing decisions are made.
-
NF_IP_LOCAL_IN - Triggered after the incoming traffic has been routed and is destined for the local host.
-
NF_IP_FORWARD - Triggered after the incoming traffic has been routed and the destination is for a remote host.
-
NF_IP_LOCAL_OUT - Triggered immediately after the locally created outbound traffic has hit the network stack.
-
NF_IP_POST_ROUTING - Triggerd by any outgoing or forwarding traffic has been routed but just before being put onto the wire.
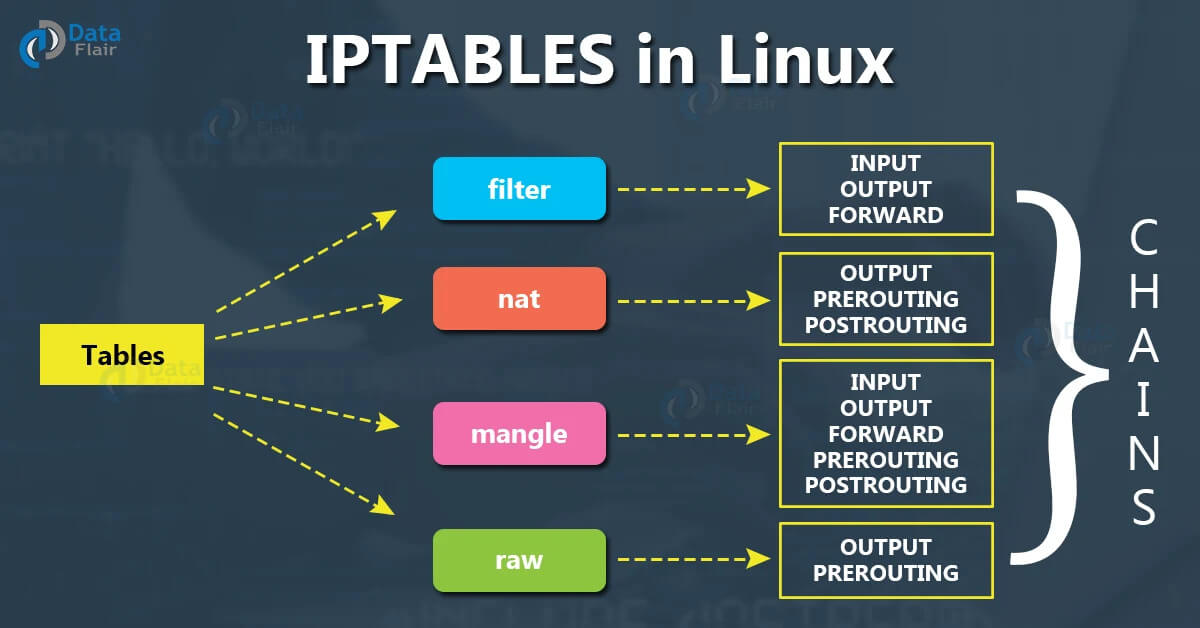
IPTables Tables & Chains#
The concepts of tables are key to understanding how iptables functions. Below we will take a look at these two concepts and how they work within iptables.
Tables#
Tables are used to classify firewall rules based on the decisions they need to make. There are 5 tables with each having a different specification.
-
FILTER - The FILTER table is used to decide if a packet will be denied or allowed. This is the usual firewall "filtering" of packets. Probably the most commonly used table when it comes to iptables.
-
NAT - The NAT table allows for network translation rules within iptables. Rules in this table determine how to modify the source or destination of a packet to impact routing decisions.
-
MANGLE - The MANGLE tables is used to alter the IP Headers of a networ packets. An internal kernel mark can be placed by also using this table. This mark does not affect the actual packet but is internal to iptables.
-
RAW - The RAW table only has the function to allow the option to mark packets to opt of out connection tracking.
-
SECURITY - The SECURITY table is only used in SELinux systems. This allows you to set internal SELinux remarks on packets.
Chains#
Within each table, rules are further organized into chains. The chain will determine when a rule is evaluated. The iptables chains essentially refer to the netfilter hook that they trigger.
-
PREROUTING - Triggered by the NF_IP_PRE_ROUTING hook.
-
INPUT - Triggered by the NF_IP_LOCAL_IN hook.
-
FORWARD - Triggered by the NF_IP_FORWARD hook.
-
OUTPUT - Triggered by the NF_IP_LOCAL_OUT hook.
-
POSTROUTING - Triggered by the NF_IP_POST_ROUTING hook.
The diagram below shows the the relationship between chains and tables.
Rules#
Rules define the conditions used to process a packet in the network. Rules are contained in the chain and use src, dst, port, protocol for packet matching. One a packet is able to match a rule it is forwarded to a target where a decision is made to determine what happens to a packet.
Targets#
Targets are simply put what happens to packet after it is matched. The list of targets are as follows:
-
ACCEPT - Allows for the packt to pass through the firewall.
-
DROP - Discards the packet and does not inform the sender.
-
REJECT - Discards the packet and notifies the sender with an error message.
-
LOG - Information about the packet is maintained in a log file.
-
SNAT - Alters the packets source IP address.
-
DNAT - Alters the destination IP for the source packet.
-
MASQUERADE - Alters a packet's source address for dynamically assigned IPs.
Commands#
- List rules
sudo iptables -L- List rules with line numbers
sudo iptables -L --line-numbers- Add rule to allow inbound HTTP traffic
sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT- Drop traffic for a specific IP address
sudo iptables -A INPUT -s [source-ip-address] -j DROP- Allow all traffic for a specific IP address
sudo iptables -A INPUT -s [IP-address] -j ACCEPTsudo iptables -A INPUT -m iprange --src-range [IP-address-range] -j REJECT- Delete a rule based on rule number
sudo iptables -D INPUT [line-number]- Accept traffic from loopback interface
sudo iptables -A INPUT -i lo -j ACCEPT- Save changes [Debian - rules are now persistant when a reboot occurs]
sudo netfilter-persistent save