How TLS works
Today we will take a look at Transport Layer Security better known as its acronym TLS. TLS is an encryption protocol designed to ensure secure communication on a network. TLS replaced the original encryption protocol known as SSL (Secure Sockets Layer). However we still use the term SSL today but really they are referring to TLS. Let’s take a look at how TLS functions and hopefully we can gain an understanding of this very important protocol.
What is the TLS handshake?
- The TLS Handshake is how two sides (client and server) agree between each other that TLS will be used to encrypt data during their communication. The TLS handshake occurs after the TCP connection has been successfully established. Once completed the TLS handshake is where the client and server will choose the TLS version, decide on cipher suites, exchange public keys, verify the SSL cert and generate sessions keys in order to use symmetric encryption after the handshake has been completed. As you can see a lot of information is passed between both sides during this sequence. Let’s look at the actual steps in the next section.
Steps in the TLS handshake
-
The exact steps in the TLS handshake can differ depending on the cipher suites supported between the client and server. Let’s take a look at the RSA key exchange algorithm as that is used most often.
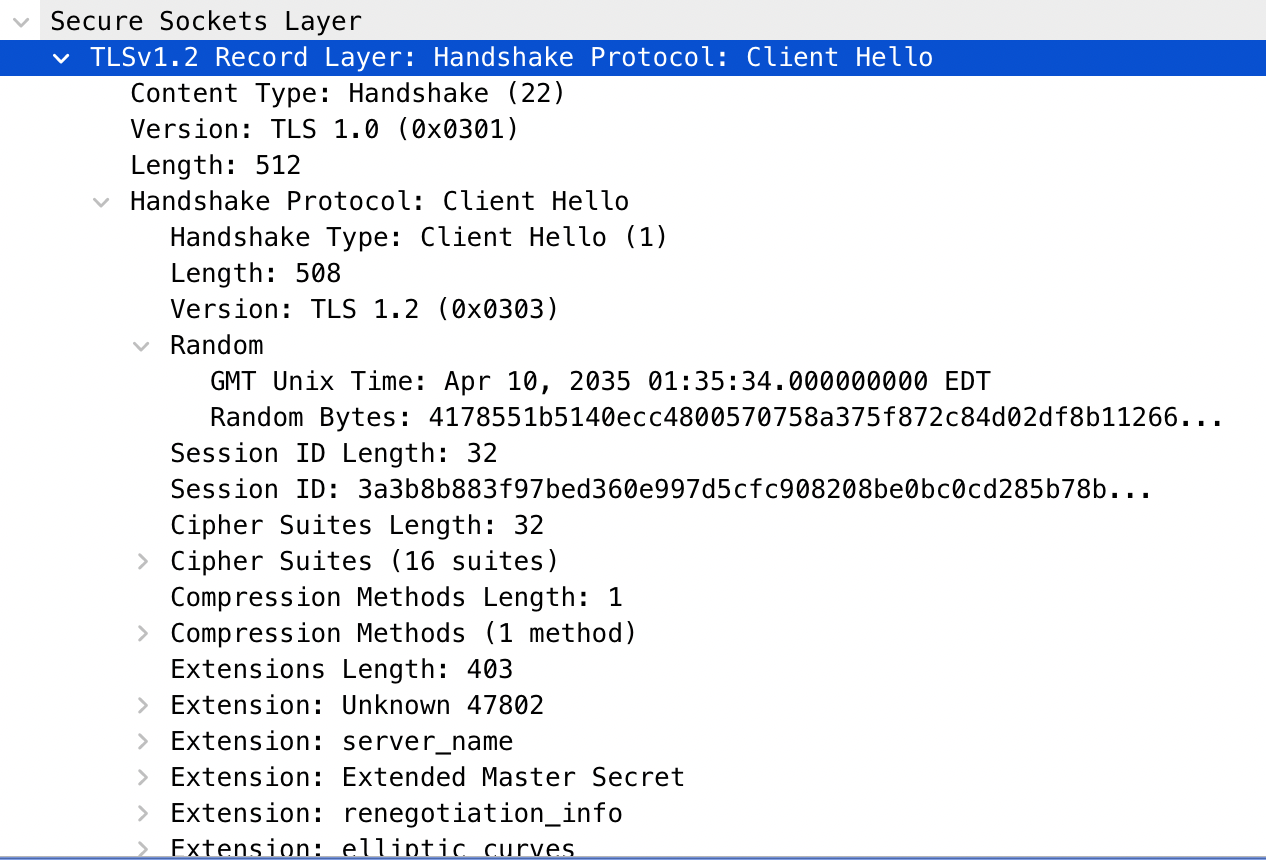
- Client Hello Message: Sent by the client and contains the following…
- TLS Version: The TLS versions supported by the client. These are listed in order of preference.
- Supported Cipher Suites: What cipher suites can the client use. These are listed in order of preference.
- Random Bytes: A string of random data generated by the client. This will be used to encrypt the data later.
- Session ID: The ID of the TLS connection.
- Compression Method: The method used for compressing the TLS packets to increase speed and lower bandwidth usage.
- Extensions: Extra TLS parameters that may be requested by the client.
- Server Hello Message: Response to the client hello message containg selected parameters from the client.
- TLS Version: The server selects a TLS version
- Cipher Suites: The server selects a cipher suite
- Random Bytes: The server creates a random 32-byte number of it’s own to use later for encryption.
- Compression Method: The server selects a compression method
-
Server Certificate: After the server hello message is sent it will send a “Certificate” message containing its SSL certificate. The public key is contained within the SSL cert.
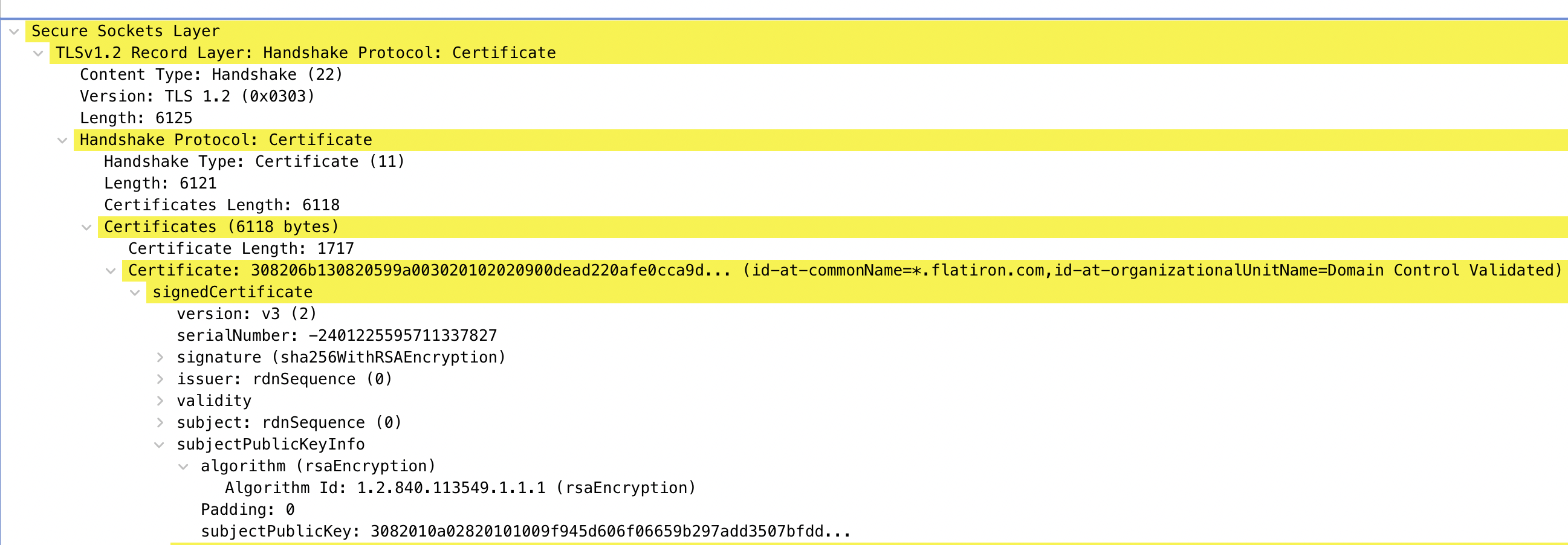
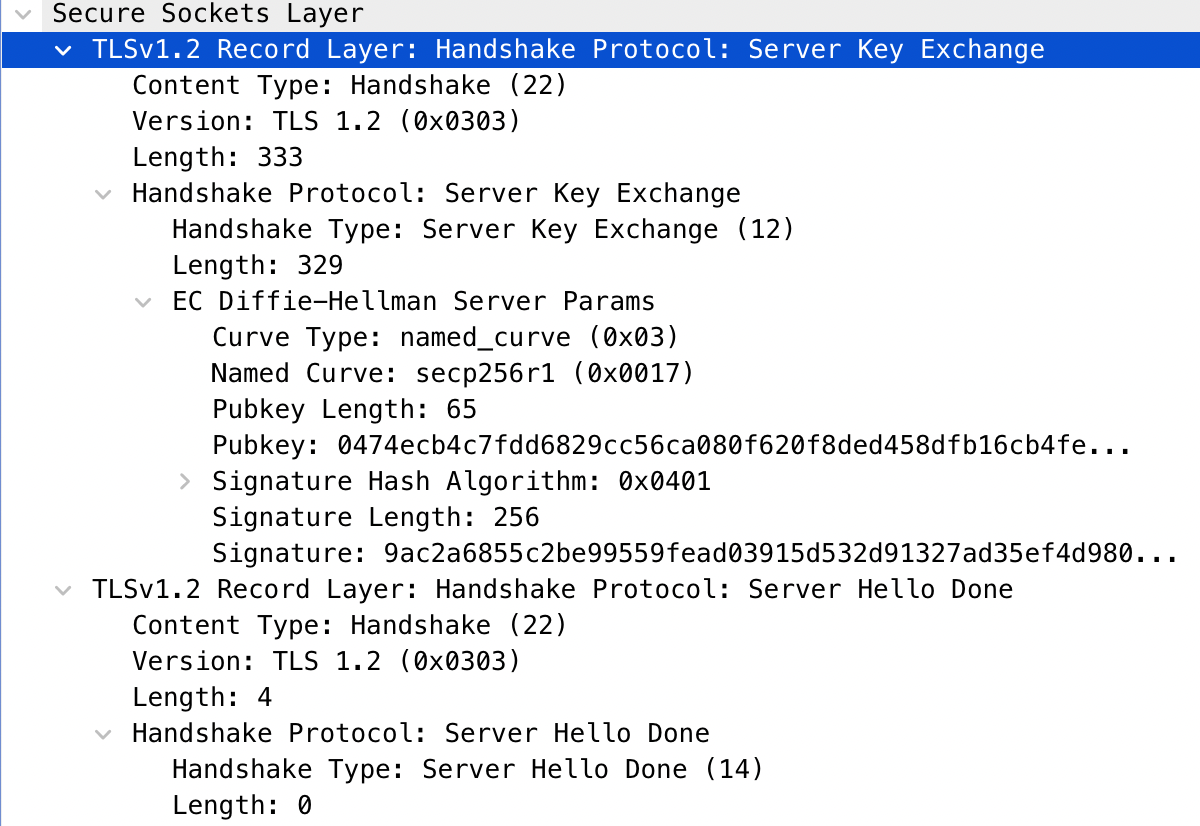
- Server Key Exchange and Server Hello Done: The server key exchange is used to send the parameters that will be used to generate the symmetric key that will be used for encrypting data. The agreed upon protocol was Elliptic Curve Diffie- Hellman Ephemeral (ECDHE) in this example. The key parameters here to take note of are as follows..
- Named Curve: The Elliptic curve selected by the server for computation.
- Public Key: The servers public key to be used by the client
- Signature: This value was signed using the private key of the server. The client will use the servers public key to verify that this belongs to the server. The Server Hello Done message is self explanatory and is the end of the Server Hello.
-
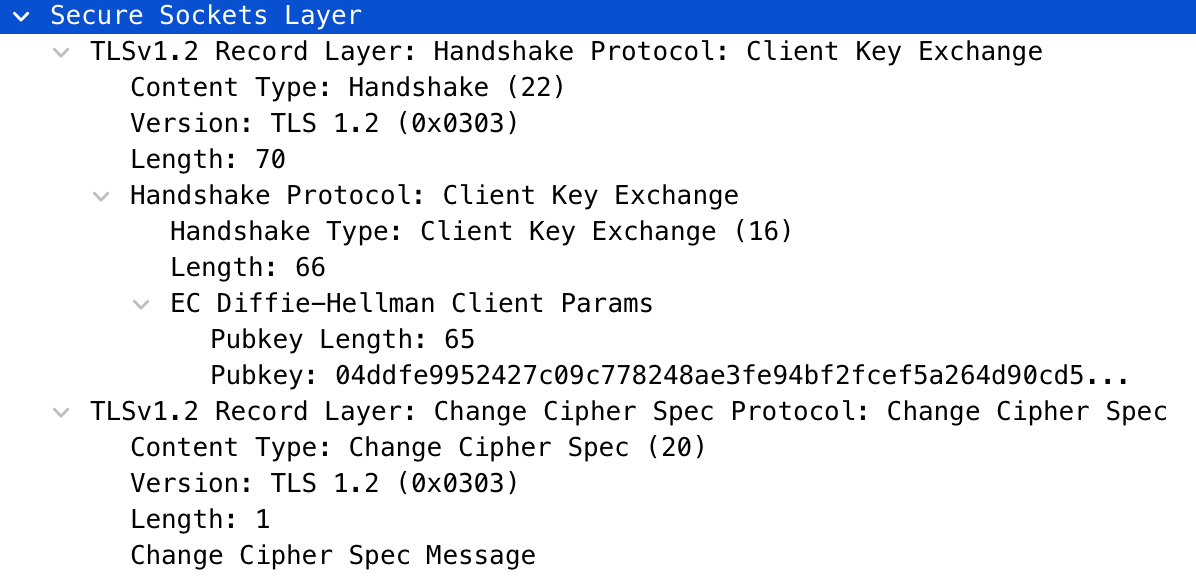
Client Key Exchange and Change Cipher Spec: The server will exchange its public paramaters for the ECDHE algorithm. The Change Cipher Spec message is used to indicate that any message sent afterwards will be encrypted using the negotiated key and algorithm.
-
Encrypted Handshake Message: This message is the final step of the TLS handshake and adds some protection from Man In The Middle (MITM) attacks. Protection from MITM is due to a HMAC-SHA256 of the master secret, hash of all messages and the finished label string is all contained here.
-
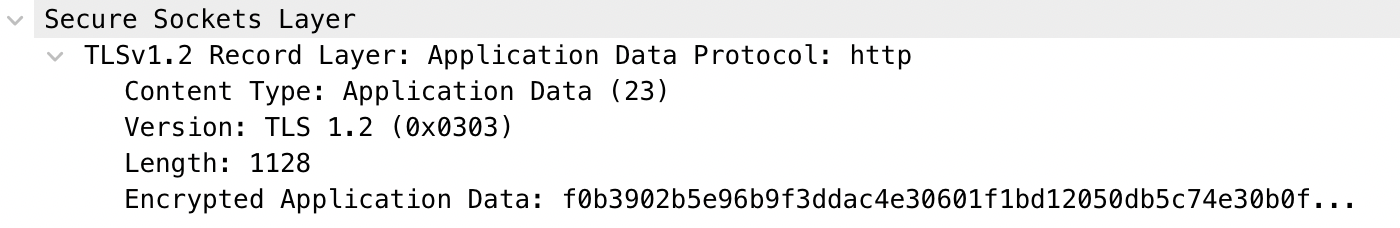
Encrypted Application Data: At this point the TLS handshake is completed and all application data is encrypted.
- Client Hello Message: Sent by the client and contains the following…
TLS Secrets
- Pre-master Secret
- Generated by the client and encrytped using the public key from the server. This is sent over to the server via the Client Key Exchange mesage. The server will decrypt it with their private key.
- Once decrypted it is used to generate the Master Key.
- Master Secret
- The Client will generate the Master secret from the initial random keys generated in the client/server hello messages and the pre-master secret.
- The Master Secret is used to derive keys for symmetric encryption.